Email Security — SPF, DKIM, and DMARC — Achieve a maximum level of security, authenticity, and…

Email Security — SPF, DKIM, and DMARC — Achieve a maximum level of security, authenticity, and integrity
Most of the attacks, either it is trojans like ransomware or spam message originates from email. Every organization uses email as the primary communication medium and According to Verizon data breach investigation report (2019), 94 % of malware is delivered through email. So, it is very important to set up the mail in a way that can prevent these types of attacks.
In this blog, I will talk about the SPF, DKIM, and DMARC and how can we set up these things to protect our organization from email threats.
SPF (Sender Policy Framework) — RFC 7208
Simply put, it is a type of DNS TXT record that includes all the servers authorized to send emails from a particular domain. Doing so helps to prevent the hacker to misuse your domain or simply prevent from being spoofed.
HOW IT WORKS?
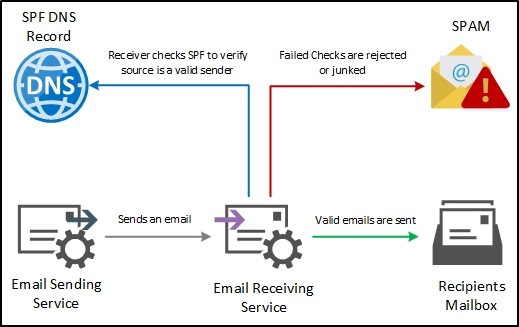
Typically, when server A sends the mail to server B. Server B looks to the return path of the mail sent by mail server A.
Now, server B takes the domain of the
return path and queries its SPF record.
Once the query completes, it searches the IP address of Server A in the returned spf records. If it finds the ip address, then spf check passes and the server will put the mail in the designated inbox. If it fails, then the message will be either rejected or stored in spam based on the configuration.
Example:
v =spf1 ip4=1.2.3.4 include:test.com ~all
The above spf record authorizes the ip, and third party domain test.com to send the email on your behalf
v=spf1 mx ~all
The above spf record authorizes the mail record of the particular domain to send the emails on your behalf.
v=spf1: it is way to let the server know that it is a spf record and every spf record starts with this string.
ip4= authorized ip address to send emails can be
listed through this syntax
include = This syntax can be added followed by domain
name to authorized third party domain send email on behalf of the domain.
mx = The mx in spf record denotes the ip address of
the mx records of the current domain.
a = The a in the spf record is the A record of the
current domain.
If SPF CHECKS FAIL, then following tags
determine what to do with the mail.
~all = soft fail — simply sends the mail to spam
-all = Fail — rejects all mail
- all = Pass = Puts the mail in inbox
DKIM (Domain Key Identified Mail)
DKIM is basically a way to authenticate an email using the digital signature which lets the receiving party to verify the integrity of the message and allows to check whether the message has been authorized by the actual owner of the domain or not.
How does it work?
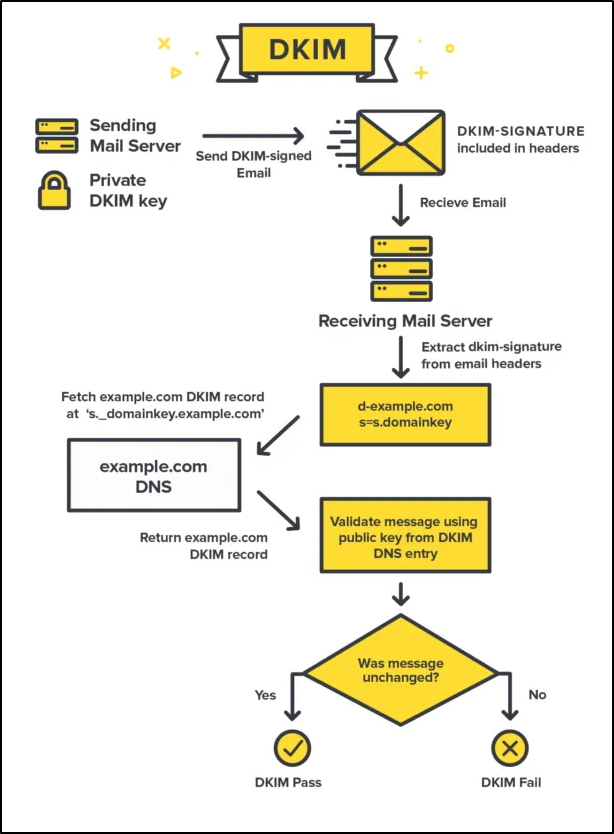
If the mail server supports DKIM and has properly configured, then the following steps go through it:
· When the sender server sends the mail, it creates a hash using the specific mail headers and body, attaches the DKIM signature in the message and forwards to the mail server.
· When a recipient receives the email, it first retrieves the public key of the sender from the DNS using the domain ‘d’ and selector ‘s’ and decrypts the signature and compares. If both value matches, then DKIM check will be pass and mail is considered as authentic otherwise it is considered as tampered and placed it into the spam.
This is how the DKIM signature looks like:
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed;
s=2013032151pm; d=google.com; h=From:Date:Subject:MIME-Version:Content-Type:Content-Transfer-Encoding:To:Message-ID;i=support@google.com;
bh=vYFvy46easdfkjdfeoe-dfcnalwpfurogh;b=iHeFQ+7rCiSQs3DPjR2eUSZSv4i/Kp+sipURfVH7BGf+SxcwOkX7X8R1RVDE1ODHhuP4I=v=1: denotes the version of DKIM
a=rsa-sha1: it denotes the algorithm used
c= relaxed/relaxed: It informs the verifier of the type of canonicalization used to prepare the message for signing. Example: relaxed/simple. Relaxed tolerates common modifications such as whitespace replacement and header field line rewrapping while simple tolerated no modifications at all.
s= It is a selector, which is used to retrieve the exact public key in case the server has multiple DKIM keys. This value makes sure that the recipient server retrieves the correct public key.
d=google.com: This name of the domain that signed the message.
h= header field included during the signing process.
l=google.com: This tag provides the email address of the signer.
bh= It is the value of body hash that is generated before message headers are signed.
b= It is the signature of the headers and body of the mail. This value is treated as empty during the verification process.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) — RFC 7489
For DMARC to work, at least SPF or DKIM must be configured for the email domain. DMARC is a type of DNS text record that tells the recipient server what to do if any the SPF or DKIM checks fail for the message going from your organization. Moreover, it also provides a mechanism to reporting, means it provides the insights of who is using your domain. This method helps to prevent your domain being used by others for cybercrimes like email spoofing, phishing.
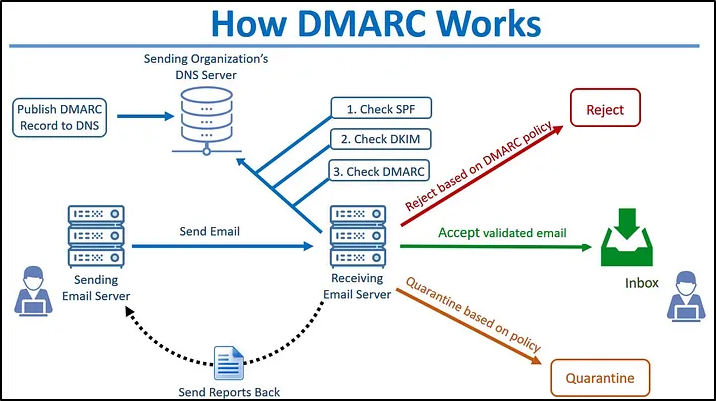
An example of DMARC policy could be
V=DMARC1, p=quarantine;
What the above example of DMARC policy does is, it simply flags the email and put it to spam if any of the record i.e., dkim or spf checks fail.
V=DMARC1;p=reject; rua=mailto:test@example.com;
The above policy will tell the recipient server to reject the email, of any of the checks fails and also sends the report to the specified mail.
There are three policies of DMARC that could be used in p tag
p=none: No action is taken
p=quarantine: Sends suspicious mail to the spam
p=reject: It does not deliver the mail.